Over the past five articles, we’ve explored the need for standardised metrics, how to make cyber risk quantification (CRQ) actionable, the mindset required to lead change, six core principles for doing it well, and the most common objections you’ll hear when trying to get started.
This is the final post in my blog series on CRQ, and the one that brings it all together.
CRQ can’t remain a pilot forever. To drive meaningful, repeatable value, it needs to mature into a business capability: trusted, embedded, and regularly informing decisions.
In this article, I share a four-stage CRQ maturity ladder. Each stage includes key actions to take, potential blockers (mapped to the objections covered in Blog #5), and traps to avoid. Together, these offer a roadmap to help CRQ evolve from a promising experiment to a business-critical capability.

Stage 1: Explore and Demonstrate Value
CRQ is still in its infancy. One or two champions are running a pilot, often with support from an external vendor. The focus is on modelling a handful of high-priority scenarios (typically ransomware) and using outputs informally to support broader conversations about cyber risk.
Actions to climb the maturity ladder:
- Identify one or two influential allies to co-sponsor the pilot.
- Run a workshop to answer: “What cyber event would disrupt our business materially?”
- Build a dashboard that contrasts CRQ outputs with traditional reporting and helps communicate uncertainty clearly.
- Document assumptions in a shared location, or in your CRQ tool if it provisions for that.
- Anchor early outputs in a consistent, decision-ready format — standard metrics build trust early (see Blog #1).
- Use early CRQ outputs to support one real-world conversation (e.g. a board update, investment case).
- Join CRQ communities or forums to accelerate learning and momentum.
Potential blocker:
"Isn't this too subjective?"
This is Objection 1 from Blog #5. Build credibility by grounding the pilot in a recent, well-known incident. Let people see that CRQ isn’t theory, it’s a structured response to real-world problems.
Common traps to avoid:
- Overpromising accuracy — Position CRQ as directional, not definitive.
- Treating outputs as final — The dashboard is a starting point, not the end product.
- Skipping success criteria — Without clear goals, it’s hard to show impact.
Stage 2: Expand Use and Build Confidence
CRQ is no longer limited to a single team. A small scenario library exists. Outputs are starting to be routinely used to support real trade-offs (e.g. shifting investment between controls). Stakeholders across risk, cyber, and finance are engaged. However, questions start to emerge about consistency, governance, and alignment with existing risk frameworks.
Actions to climb the maturity ladder:
- Build a stakeholder engagement matrix (see the below visual to aid your thinking).
- Use CRQ to inform a real decision (e.g. prioritise spend, optimise cyber insurance).
- Draft a six-month CRQ roadmap to clarify what you'll model and why.
- Align analyses to a clear business objectives — ideally linked to areas like risk appetite or capital exposure.
- Integrate CRQ outputs into governance decks (e.g. board updates, investment papers).
- Create a lightweight review cycle, with a named challenger for each refresh.
- Develop a reusable 'CRQ 101' explainer deck to onboard new stakeholders.
- Translate CRQ outputs into language that aligns with enterprise risk frameworks.
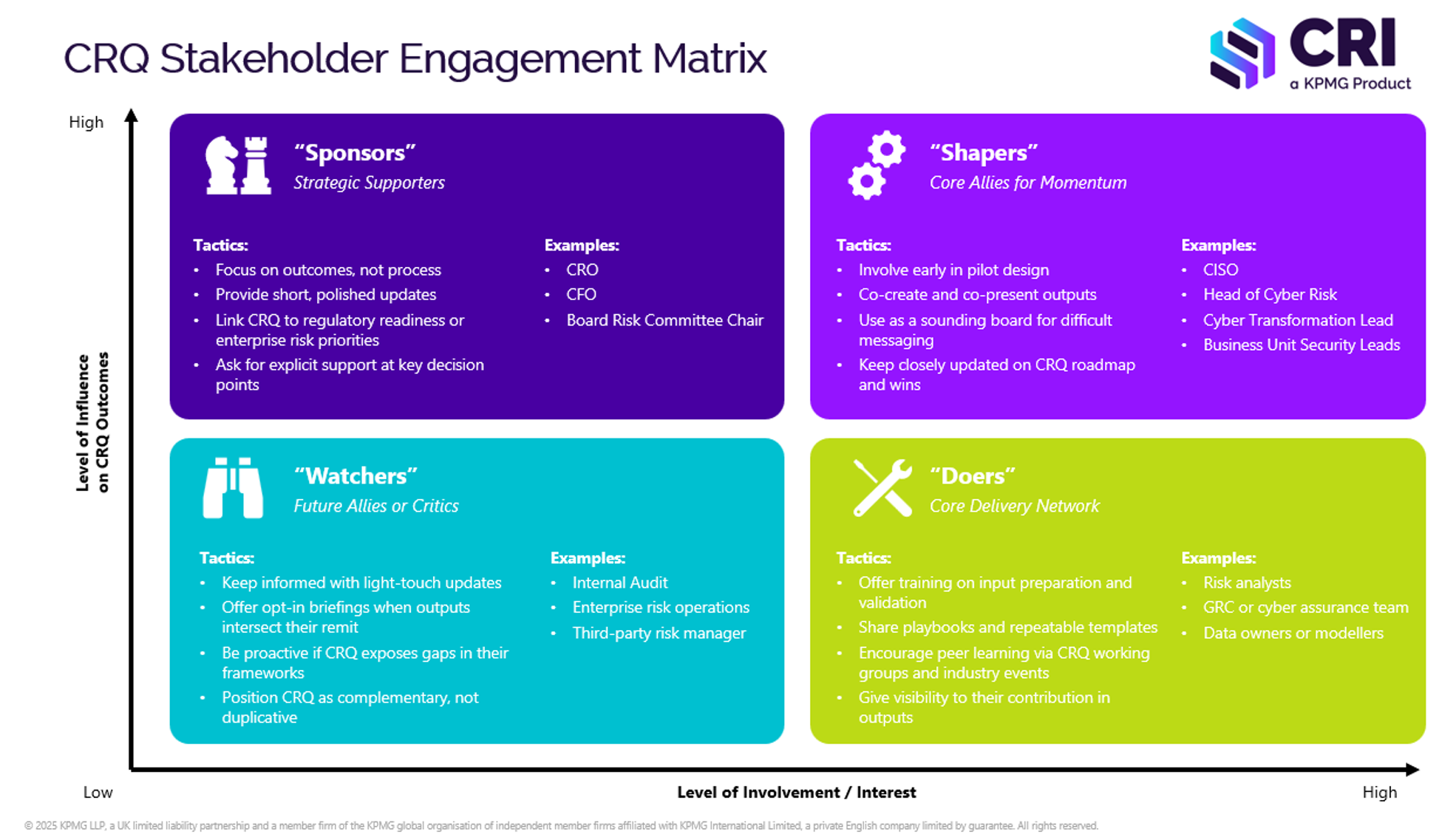
Potential blocker:
“What if this contradicts existing narratives?”
This is Objection 4 from Blog #5. Start by showing alignment with current frameworks. Then use CRQ to add nuance where needed, not to replace what’s already working.
Common traps to avoid:
- No socialisation — Outputs may land flat if key people see them too late.
- Misaligned with ERM — CRQ might be side-lined if it jars with established risk views.
- Too much jargon — Translate CRQ into business terms to keep credibility.
Stage 3: Standardise and Operationalise
CRQ is now embedded in key decisions. Outputs inform business cases, investment boards, and capital planning. The process is repeatable, the language is clearer, and delivery is largely internal, with targeted support from CRQ providers as needed.
Actions to climb the maturity ladder:
- Revisit Blog #3 and ensure practitioners are empowered and visible as change agents.
- Publish a CRQ playbook: how you scope, model, validate, and communicate.
- Launch a monthly CRQ working group with 5-8 champions across the business.
- Embed CRQ into at least two standing decision forums (e.g. ops or board risk committees).
- Align outputs with enterprise risk tools (e.g. risk appetite, tolerance statements, capital models).
- Standardise reporting templates to promote consistent messaging.
- Nominate a CRQ lead per function to support decentralised usage.
- Revisit risk appetite — use CRQ to test and tune thresholds.
Potential blocker:
“How do we know it's accurate?”
This is Objection 2 from Blog #5. Explain that CRQ is calibrated expert judgment — transparent, grounded in reference events, and consistently applied.
Common traps to avoid:
- Siloed ownership — CRQ must be relevant across functions to deliver value.
- Outdated estimates — Refresh at least quarterly or when risk conditions change.
- Assuming understanding — Repetition, framing, and interpretation guidance are essential.
Stage 4: Embed as Capability
CRQ is now a business-wide capability. It supports enterprise risk, finance, resilience, and strategic planning. It has governance, rhythm, executive sponsorship, and visible impact. CRQ isn't a project, it's how the organisation talks about cyber risk.
Actions to climb the maturity ladder:
- Formalise a CRQ operating model (governance, people, process, data and tooling).
- Link scenario refreshes to annual planning, budgeting, and capital allocation cycles.
- Build a CRQ performance dashboard (e.g. % of scenarios reviewed, decisions informed).
- Review CRQ usage across teams to identify where it's landing well and where it isn't.
- Refresh stakeholder engagement plans annually — as people, teams, and politics change.
- Use CRQ to demonstrate alignment with DORA, NIS2, or resilience expectations.
- Celebrate CRQ 'exemplars' across the business — behaviour reinforces maturity.
- Reground the team in the six CRQ working principles (See Blog #4).

Potential blocker:
“Isn’t this just business as usual now?”
The risk here is complacency. Use the six CRQ principles from Blog #4 to assess whether the capability is staying sharp or drifting.
Common traps to avoid:
- Automation without adoption — Process is just important as the tooling.
- Stale assumptions — Even familiar scenarios need regular challenge.
- Insight without action — As per Blog #2, CRQ is useful only when it drives decisions.
Final Thoughts: CRQ Grows with Use
CRQ doesn’t reach maturity through one well-run pilot. It grows by being used, and being useful, again and again.
If there's one message across this blog series, it's that CRQ is both a mindset and a method. An art and a science. It can give us sharper insights, but more importantly, it helps us make better decisions. Not in theory, but in practice. Not just in cyber, but across the business.
Here’s a quick recap of the series:
- Blog #1: Why we need standardised CRQ metrics
- Blog #2: Making CRQ results actually useful
- Blog #3: The mindset and role of the CRQ practitioner
- Blog #4: Six working principles of effective CRQ
- Blog #5: Overcoming the five most common CRQ objections
- Blog #6 (this one): How to operationalise CRQ as a lasting capability
Wherever you are on your CRQ journey — pilot, expansion, standardisation, or enterprise capability — I hope this series has helped you find clearer language, stronger arguments, and more practical ways to lead.
If you’d like to have a chat about how we help clients make this feel real, feel free to each out to me or the Cyber Risk Insights team.